
Protect Your Business from Digital Threats: Ways To Keep Your Data Safe
Digital security breaches threaten every company, from the smallest family businesses to the largest corporations. That’s why it’s essential to know how to protect your data from prying eyes.
Here are some simple steps you can take to keep yourself safe from cybercrime.
What is a Data Breach?
A data breach is a security incident where unauthorized access to confidential, sensitive, or protected information is copied, sent, viewed, stolen, altered, or used for fraudulent purposes. Hackers are looking to use this stolen information to aid in crimes such as identity fraud. Anyone can be at risk including:
- Individuals
- Organizations
- Small businesses
- High-level enterprises
- Governments
Remember that anyone can put you at risk if your information is not protected. Due to weaknesses in technology and user behavior, data breaches can happen. As technology evolves, data is more susceptible. It becomes more challenging to protect our technology as it continues to grow.
Common Types of Data Breaches
You should be familiar with these common types of breaches:
- Malicious attacks. These happen due to glitches or gaps in the cloud, third-party software weaknesses, and easy-to-guess passwords.
- Insider data breach. Someone who works for or is involved with a company purposely leaks information.
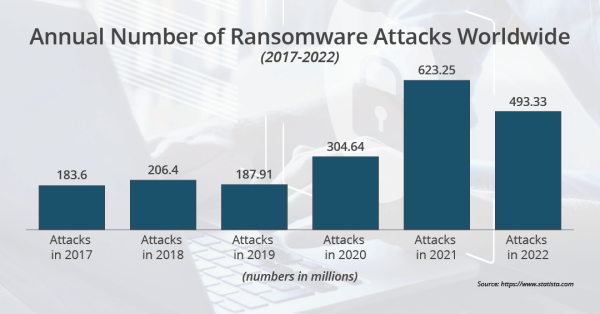
- Destructive and ransomware attacks. Someone destroys records or holds them for ransom.
- Brute force attacks. Hackers will go through every password possibility until they get it correct. Malware may be used to speed up the process.
- Nation-state attacks. Hackers work with a government to commit a crime against the U.S. or its allies.
- Stolen information. Someone leaves a computer on with valuable information to steal or files a document where they shouldn't have.
- Phishing. Third-party hackers create sites or emails that look legit to steal personal information. Cybercriminals can also use voice and text messaging.
Targeting and damage
Remember that hackers learn the weak points and develop a strategy to get users to mistakenly download malware. They may attack the network directly, giving them the freedom to search for data. On average, it takes more than five months to detect a breach.
Cybercriminals typically target:
- Weak credentials
- Stolen credentials
- Compromised assets
- Payment card fraud
- Third-party access
- Mobile devices
Data breaches can have long-lasting and severe effects to your business’ continuity. It not only is it devastating to the organization, but people may remember you more for the data breach than your business operations and brand. When it comes to the consequences of a data breach, companies may endure:
- Financial loss
- Damage to brand reputation
- Loss of customer trust
- Operational disruptions
- Legal consequences
- Cost of downtime
- Loss of private data
- Regulatory fines
- Loss of productivity
Make sure to investigate whether your data has been compromised. The longer it goes undetected, the more harm comes to your business.
Dealing with a Data Breach
If your business has a breach, you should:
- Act within the first 24 hours.
- Identify the source and extent of the breach. Find out the data affected by the breach.
- Name a team of key leaders from each department and assign roles and responsibilities.
- Take security to the next level by fixing the issue in your security and training your employees.
- Talk with legal authorities.
- Notify those affected and eliminate the breach.
The Federal Trade Commission is here to help make sound decisions with their data breach response guide for businesses. The guide breaks down steps you should take to contain and fix a data breach from securing your operations to notifying the appropriate parties.
Protect Your Data
To keep data secure, everyone can lend a helping hand, no matter what department you work in.
If you’re handling customer data, you'll need:
- A strong firewall. It can serve as a first line of defense against hackers.
- Good encryption. This cybersecurity measure converts information or data and can only be accessed by users with a decryption key – a secret code or password. For instance, websites use a secure socket layer (SSL) to encrypt data when it’s sent back and forth.
- A reliable antivirus system. Frequent updates protect you against the latest threats and attacks. Make sure to update the software often.
- Secure file-sharing software. This involves safely and securely sending data between users to prevent unauthorized access.
Most importantly, you should frequently back up data, so your system restores quickly with the most current data.
Train Your Team
Not all data breaches are the fault of malicious hackers — your own employees can expose your business' private data.
Most hackers use social engineering tactics as opposed to brute force. Social engineering uses manipulation, influence, and deception to gain control of a victim’s computer or to steal sensitive information. These include phishing, baiting, and pretexting attacks. Therefore, a well-versed workforce is essential to protecting your data. Teach your team about the basics:
- Creating strong passwords.
- Keeping private email accounts separate from work email.
- Being skeptical about email offers.
- Reporting any suspicious activity promptly.
If your employees take computer equipment offsite, make sure to encrypt and protect phones, tablets, and laptops with secure passwords. Don't allow employees to connect private USB drives or personal devices to workplace computers.
Data breaches aren’t always digital – breaches can occur when hard copy files are left unattended. These are also targets for theft. You can teach your team:
- Clean-desk policy. Employees should not leave any files visible at the end of the workday.
- Retention guidelines. Businesses may be required to keep documents on file for one, three or seven years. Some may need to be kept indefinitely. Federal and state law have requirements depending on the industry or circumstances. Check with an accountant, lawyer or record-keeping agency for guidance.
- Shredding procedures. If your team can't destroy documents in a timely manner, schedule a service to shred your files.
Learn To Protect Yourself
Protect yourself from scams and fraud by becoming aware of various digital threats on the Internet. Check out our fraud protection section to get the latest news in scams and fraud and how to protect yourself.
The information in this article was obtained from various sources not associated with Adirondack Bank. While we believe it to be reliable and accurate, we do not warrant the accuracy or reliability of the information. Adirondack Bank is not responsible for, and does not endorse or approve, either implicitly or explicitly, the information provided or the content of any third-party sites that might be hyperlinked from this page. The information is not intended to replace manuals, instructions or information provided by a manufacturer or the advice of a qualified professional, or to affect coverage under any applicable insurance policy. These suggestions are not a complete list of every loss control measure. Adirondack Bank makes no guarantees of results from use of this information.

